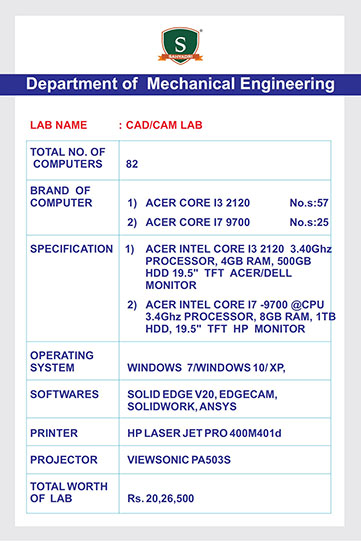
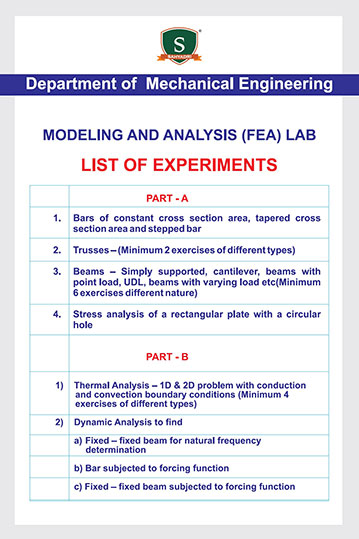
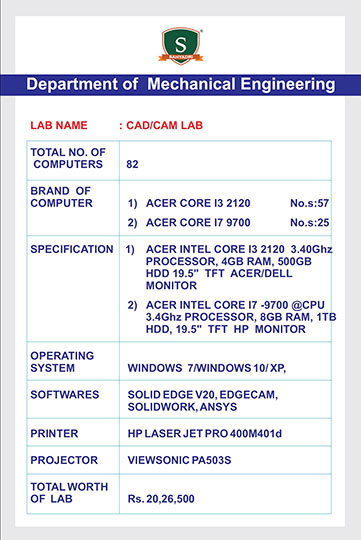
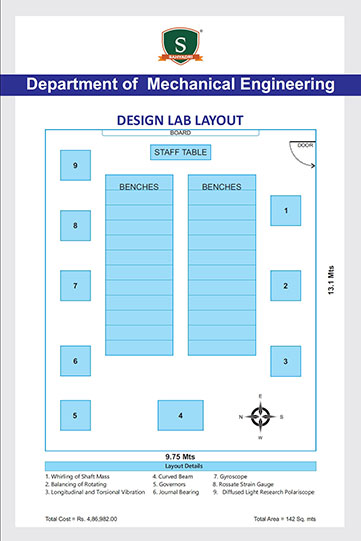
Day-Two of Five Days Online FDP on “Research Challenges and Trends in Information Technology”
05-Aug-2020
Day-Two of the Online Faculty Development Program (FDP) on “Research Challenges and Trends in Information Technology” had two sessions.
The Resource Person for Session-1 was Dr. Geetha V., Asst. Professor, Dept. of Information Technology-NITK Surathkal. The Agenda was focused more on Research Trends in Internet of Things and its challenges.
Highlights of the Session:
• Introduction to Internet of Things: 3A Concept- Anytime, Anywhere and Any media, resulting into sustained ratio
• Architecture of Internet of Things: Radio Frequency Identification(RFID), Service-Oriented Architecture, Wireless Sensor Networks
• Applications of Internet of Things: Smart Homes & Cities, Security, Building Management, Healthcare, Agriculture and Travel.
• Challenges of Internet of Things: Regulation & Policy Issues, Data Protection, Device Liability, Security and Privacy
• Future trends in Internet of Things and its benefits
• Internet of Things Technologies and Trends
• Research Challenges in IoT
About the Resource Person:
Dr. Geetha V. comes with a total of 20 years of academic experience. Her area of interest is Communication Technologies for Wireless Sensor Networks, Internet of Things and Home Automation System. She has published more than 30 publications in reputed journals and conferences.
The Resource Person for Session-2 was Mr. Santosh Chaluvadi, Founder & CEO-Supraja Technologies. The Agenda was focused on Role of Cyber Security in Internet of Things.
Highlights of the Session:
• Demonstration on how the Email address can be compromised via haveibeenpwned.com, where the compromised data could be Email address, Geographical Locations, name, password, Username
• The following immediate actions to be taken in Case Data is being compromised:
? Setting secure passwords using howsecureismypassword.net
? Enabling Two-step verification in settings
• Mobile Security - To verify whether Mobile is hacked or not, the following steps need to be taken:
? Installation of Root Checker Application to check their device for root (Administrator, Superuser) access
? SEP Mobile Application by semantic to analyze the Malware information in detail and take necessary action
? Spyware Detector Application to remove spyware
? Glasswire Data usage Monitor Application to monitor your mobile data usage, data limits and WiFi Network activity
? Installation of unknown apps, setting Finger Lock and App lock,
? KeyScrambler Application to encrypt the data entered from the keyboard
About the Resource Person:
Mr. Santosh Chaluvadi, a young entrepreneur, is a Digital Marketer by profession and security enthusiast by passion. He primarily focuses on content building, testing and monetization of blogs. Besides Ethical Hacking and Cyber Security, he also has a passion for Blogging and Digital Marketing.