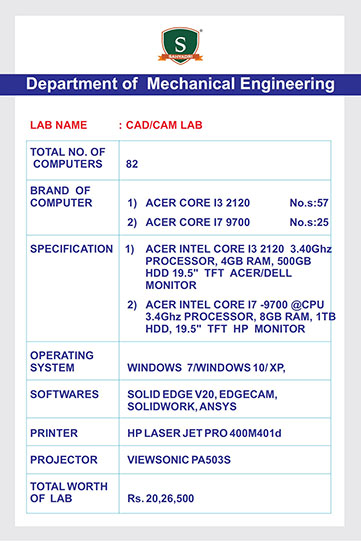
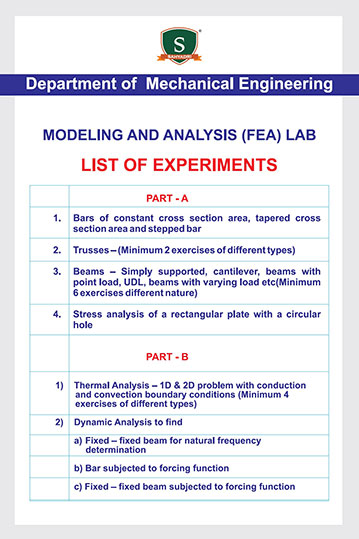
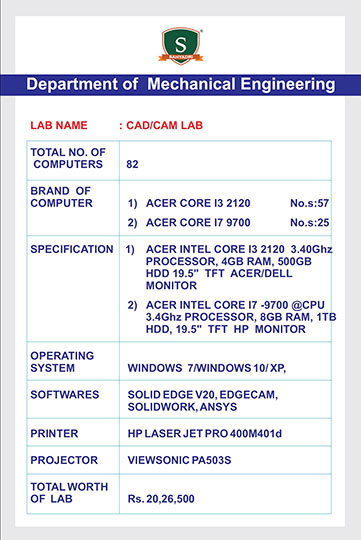
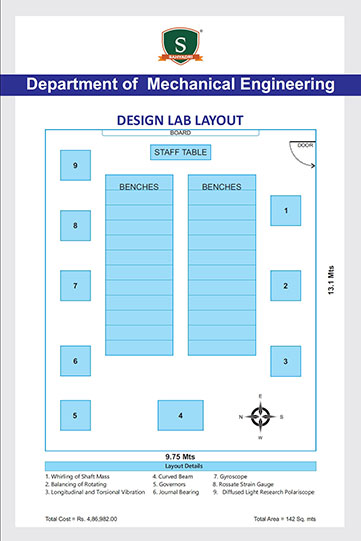
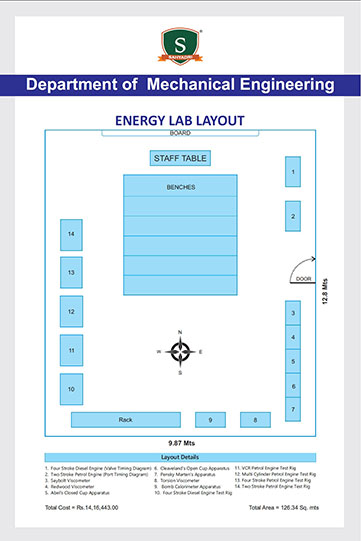
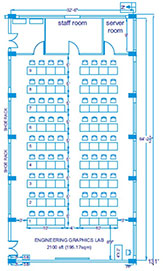
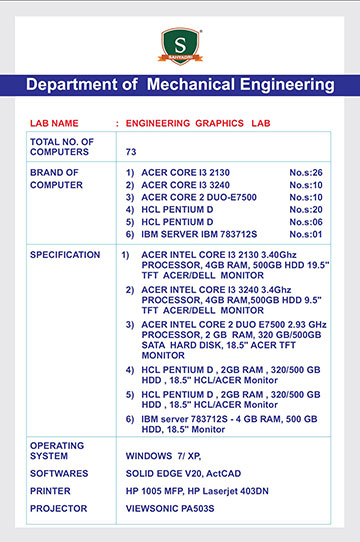
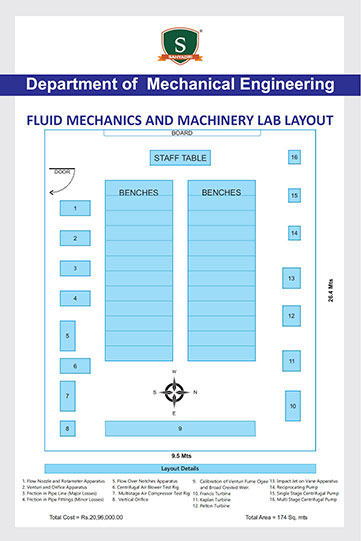
As a part of the ISEA (Information Security Education and Awareness), a Govt of India initiative, Dept of MeitY and CDAC, a workshop was organized for the CIO's (Chief Information Officers) of various MNCs of India
17-Mar-2021
Dr. Ananth Prabhu G, Professor in the Department of Computer Science & Engineering and Principal Investigator of the Sahyadri Digital Forensics and Cyber Security Laboratory addressed the 150+ participants on Privacy and Anonymity.
Key Points:
1. With the development of the Internet, personal information is becoming more and more transparent. For preventing the information leakage, many security teams are interested in developing anonymous protection of the operating system. Qubes OS, Tails, Whonix, Linux Kodachi are some of the privacy centric OS.
2. Privacy and anonymity are two different concepts. They are both increasingly necessary as we get increasingly wiretapped and tracked, legally so or not, and it’s important to understand why they are an integral part of our civil liberties – why they are not just beneficial to the individual, but absolutely critical to a free society.
3. Privacy is the ability to keep some things to yourself, regardless of their impact to society. To take a trivial example, I lock the door when I go to the men’s room – not because I’m doing something criminal or plotting to overthrow the government in the men’s room, but simply because I want to keep the activity there to myself.So privacy is a concept describing activities that you keep entirely to yourself, or to a limited group of people.
4. In contrast, anonymity is when you want people to see what you do, just not that it’s you doing it. The typical example would be if you want to blow the whistle on abuse of power or other forms of crime in your organization without risking career and social standing in that group, which is why we typically have strong laws that protect sources of the free press. You could also post such data anonymously online through a VPN, the TOR anonymizing network, or both. This is the analog equivalent of the anonymous tip-off letter, which has been seen as a staple diet in our checks and balances.
5. Publishing on social media today is more permanent than chiseling hieroglyphics in stone. Take a step back and consider the whole picture of what you're sharing.