Dept. of Mechanical Engineering – “VTU Visualizing Engineering” kicks off

VTU sponsored CAE (Computer aided engineering) training titled "VTU Visualizing Engineering" started today 2nd Aug, 2021 at 9AM with Prof. Karisiddappa, VC of VTU inaugurating the session. The training is held by VTU in collaboration with ALTEM Technologies in the CAE skills using MSC software - MSc Nastran/Patran (Complete FEA Modeling Solution), Msc Adams (Multibody Dynamics Simulation), MSC Apex (Unified CAE Environment for Virtual Product Development), MSC Fatigue(For fatigue analysis), MscMarc (Advanced Nonlinear Simulation Solution), Msc ScFlow, Msc Sinda (Advanced Thermal Simulation), MSc Easy5 (Advanced Controls & Systems), MSc Digimat (Nonlinear Multi-scale Material and Structure Modeling) and MSc Simufact (Manufacturing Process Simulation).
The training is based on "Train the Trainer" model wherein each engineering college has a COE team of faculty who will train the rest of faculty and students after this training. The training is from 2nd August to 4th October 2021 from 9 AM to 6 PM. The COE team consists of - Dr. Rathishchandra R Gatti (COE Coordinator), Mr. Lawrence Fernandes, Mr Kiran Prakash, Mr.Vikas G and Mr. Naveen B.
MSc software, especially NASTRAN was developed for NASA and later adopted in aerospace, automotive and other industries for engineering design. Hence, the department is actively planning to associate the MSC packages with assignments and projects in the curriculum so that students learn industry ready skills for employability.
Talent Selection Bootcamp at Sahyadri by IIC Sahyadri
Sahyadri in collaboration with InUnity Mangaluru successfully hosted a 2-Day Talent Selection Bootcamp to foster an Entrepreneurial Mindset in students. It was conducted to encourage students to use the existing tools to swiftly build solutions to the problems given at the instant of the Bootcamp.
The Bootcamp familiarised the students with the process of design thinking, research methods and rapid prototyping tools to propose solutions for the problems given during the Bootcamp. It assessed the involvement of the students, their resilience to handle pressure and their self-learning attitude to shortlist students with the mindset to solve bigger challenges.
Placement and Training
Hourglass Research

Hourglass Research provided placement opportunities for the B.E./B.Tech/M.E./M.Tech - Electronics, Electronics & Telecom, Electrical & Electronics 2021 batch for the position of Patent Associate. Package which was offered was ₹ 5.5 LPA.
About Company: Hourglass Research is a leading Intellectual Property (IP) end-to-end solutions provider helping organizations around the world secure, manage and monetize their IP assets. They cater to a global clientele that includes “Fortune” listed corporations, law firms, SMEs, start-ups and VCs. Founded in 2010, Hourglass Research aims to help customers gain a competitive advantage by leveraging their IP opportunities. With offices strategically located in Silicon Valley, California, and in India, they have been ensuring customer delight by leveraging on value and time zone advantages.
Amazon Internship opportunity

Amazon provided Internship opportunity for Btech, B.E, M.Tech 2021, 2022 outgoing batch. They have offered Stipend of INR 30,000 Per Month. This opportunity was to collaborate with experienced cross-disciplinary Amazonians to conceive, design, and bring innovative products and services to market.
About Company: Amazon is guided by four principles: customer obsession rather than competitor focus, passion for invention, commitment to operational excellence, and long-term thinking. Amazon strives to be Earth’s most customer-centric company, Earth’s best employer, and Earth’s safest place to work. Customer reviews, 1-Click shopping, personalized recommendations, Prime, Fulfillment by Amazon, AWS, Kindle Direct Publishing, Kindle, Career Choice, Fire tablets, Fire TV, Amazon Echo, Alexa, Just Walk Out technology, Amazon Studios, and The Climate Pledge are some of the things pioneered by Amazon.

Day Thirty Nine of CET Crash Course for CET Aspirants
This space gives a glimpse of the Day-Wise information related to CET Crash Course organized for CET Aspirants at 10:00 am to 1:00 pm every day.
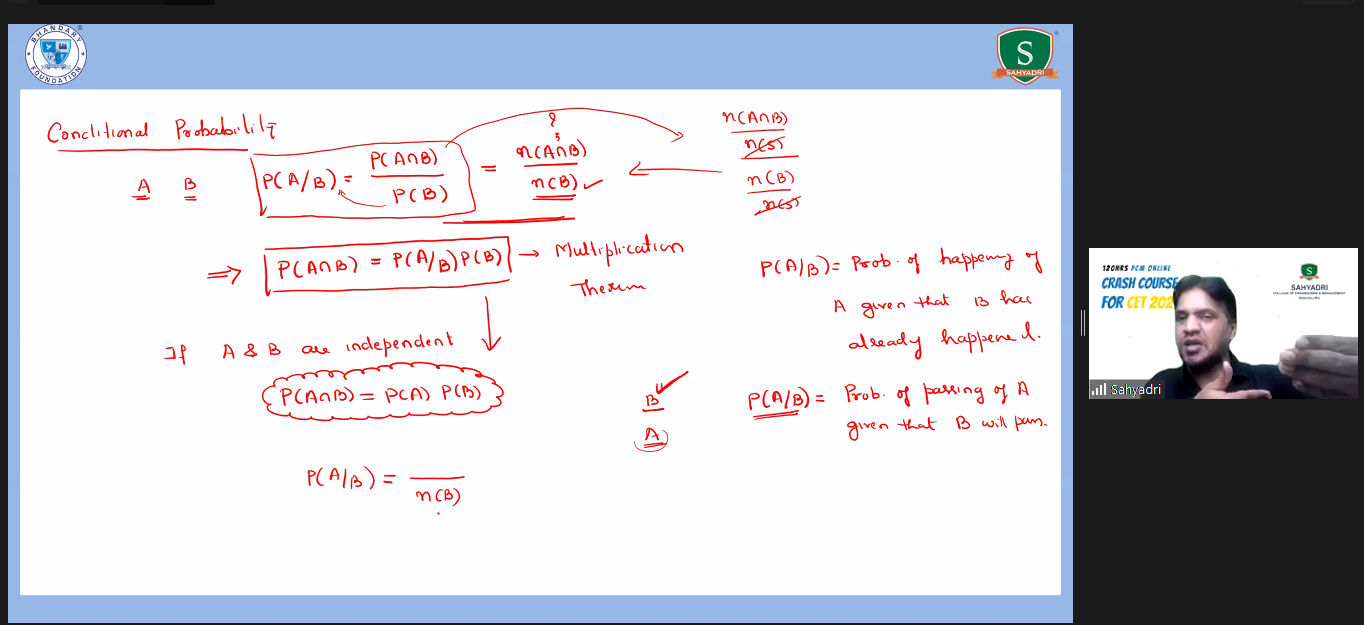
Subject: Mathematics
Topic: Probability
Participant Count: 1,293
Top 10- Most Common Types of Cyber Attacks
 Continued…
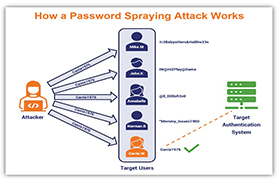
• Password attack:
Continued…
• Password attack:
As passwords are the most commonly used authentication for validating the authenticity of users to an information system, obtaining passwords is a common and effective attack approach. Access to a person’s password can be obtained by looking around the person’s desk, ‘‘sniffing’’ the connection to the network to acquire unencrypted passwords, using social engineering, gaining access to a password database or outright guessing. The last approach can be done in either a random or systematic manner;
• Brute-force password guessing means using a random approach by trying different passwords and hoping that one of it will work Some logic can be applied by trying passwords related to the person’s name, job title, hobbies, or similar items.
• In a dictionary attack, a dictionary of common passwords is used to attempt to gain access to a user’s computer and network. One approach is to copy an encrypted file that contains the passwords, apply the same encryption to a dictionary of commonly used passwords, and compare the results.
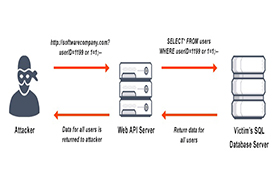
• SQL injection attack:
SQL injection has become a common issue with database-driven websites. It occurs when a malefactor executes a SQL query to the database via the input data from the client to the server. SQL commands are inserted into data-plane input (for example, instead of the login or password) in order to run predefined SQL commands. A successful SQL injection exploit can read sensitive data from the database, modify (insert, update or delete) database data, execute administration operations (such as shutdown) on the database, recover the content of a given file, and, in some cases, issue commands to the operating system.
In order to protect yourself from SQL injection attacks, apply least0privilege model of permissions in your databases. Stick to stored procedures (make sure that these procedures don’t include any dynamic SQL) and prepared statements (parameterized queries). The code executed against the database must be strong enough to prevent injection attacks. In addition, validate input data against a white list at the application level.
To be continued…
Quote for the day
Keep your face to the sunshine and you cannot see a shadow.
- Helen Keller