Placement and Training: MissionEd - Internship Program

MissionEd is launching the applications of internship programs for a diverse range of profiles.
MissionEd is one of India's leading Edtech startups catering to students of classes 8-12. Founded by students of IIT Delhi, IIT Kharagpur and IIT Kanpur in March 2020, MissionEd aims to revolutionize the learning experience of students by bringing in gamification and quality content at a low cost. Recognized as one of India's top 20 rising Edtech startups in 2020, MissionEd has transformed the lives of 2500+ students all over the country so far.
Interested candidates can register at:
https://tiny.one/internmissioned

Day Forty of CET Crash Course for CET Aspirants
This space gives a glimpse of the Day-Wise information related to CET Crash Course organized for CET Aspirants at 10:00 am to 1:00 pm every day.
Subject: Mathematics
Topic: Three Dimensional Geometry and Statistics
Participant Count: 1,293
Top 10- Most Common Types of Cyber Attacks
Continued…
• Cross-site scripting (XSS) attack:
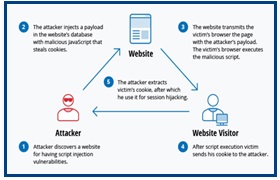
XSS attacks use third-party web resources to run scripts in the victim’s web browser or scriptable application. Specifically, the attacker injects a payload with malicious JavaScript into a website’s database. When the victim requests a page from the website, the website transmits the page, with the attacker’s payload as part of the HTML body, to the victim’s browser, which in turn executes the malicious script.
For example, it might send the victim’s cookies to the attacker’s server, and the attacker can extract it and use it for session hijacking. The most dangerous consequences occur when XSS is used to exploit additional vulnerabilities. These vulnerabilities can enable an attacker to not only steal cookies, but also log keystrokes, capture screenshots, discover and collect network information, and remotely access to gain control of the victim’s machine.
While XSS, that’s within VBScript, ActiveX and Flash can be jeopardized, the most widely abused is JavaScript — primarily because JavaScript is supported widely on the web.
To defend against XSS attacks;
• Developers can sanitize User data input in an HTTP request before reflecting it back.
• Make sure that, all data is validated, filtered, or escaped before echoing anything back to the user, such as the values of query parameters during searches. Convert special characters such as? & , /, <, > and spaces to their respective HTML or URL encoded equivalents.
• Give users the option to disable client-side scripts.
• Eavesdropping attack:
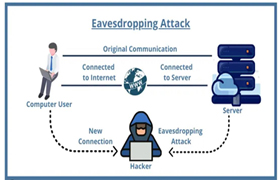
Eavesdropping attacks occur through the interception of network traffic. By eavesdropping, the attacker can obtain passwords, credit card numbers, and other confidential information that a user might be sending over the network.
Eavesdropping can be passive or active;
Passive eavesdropping — A hacker detects the information by listening to the message transmission over the network.
Active eavesdropping — A hacker actively grabs the information by disguising himself as a friendly unit and by sending queries to transmitters. This is called probing, scanning, or tampering.
Detecting passive eavesdropping attacks is often more important than spotting active ones, since active attacks require the attacker to gain knowledge of the friendly units by conducting passive eavesdropping before.
Data encryption is the best countermeasure to tackle eavesdropping.
To be continued…
Quote for the day
Keep your face to the sunshine and you cannot see a shadow.
- Helen Keller