Placement and Training: Webonise – Internship Program

Webonise is a product development company with 200+ talented software engineers, usability experts, product managers and quality assurance. Webonize builds app and mobile experiences that people love.
Interns will be entitled for an amount of INR 12,000/- (Twelve Thousand Only) per month as stipend during the tenure of their internship. Internship Period is 4 months. On confirmation, the compensation will be INR 3.6 LPA + 50k bonus.
Interested candidate can apply by
https://docs.google.com/forms/d/e/1FAIpQLSe7__gF8ZdzOhtCpFDXiKRCrCX-8VLeiZOFuoVq0fJQ-h_MKg/formrestricted

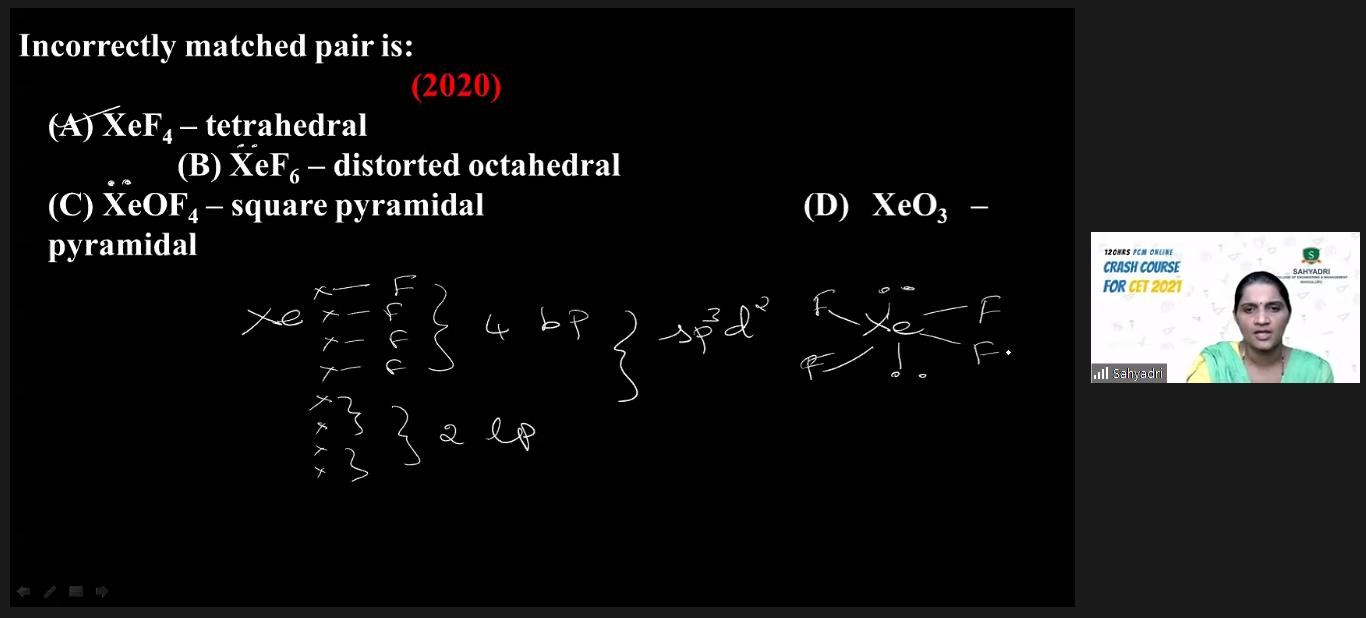
Day Forty One of CET Crash Course for CET Aspirants
This space gives a glimpse of the Day-Wise information related to CET Crash Course organized for CET Aspirants at 10:00 am to 1:00 pm every day.
Subject: Chemistry
Topic: p, d and f Block Elements
Participant Count: 1,056
Top 10- Most Common Types of Cyber Attacks
Continued…
•
Birthday attack:

Birthday attacks are made against hash algorithms that are used to verify the integrity of a message, software, or a digital signature. A message processed by a hash function produces a message digest (MD) of fixed length, independent of the length of the input message; this MD uniquely characterizes the message. The birthday attack refers to the probability of finding two random messages that generate the same MD when processed by a hash function. If an attacker calculates the same MD for his message as the user has, he can safely replace the user’s message with his, and the receiver will be unable to detect the replacement even if he compares MDs.
• Malware attack:
Malicious software can be described as unwanted software that is installed in your system without your consent. It can attach itself to legitimate codes and propagate; it can lurk in useful applications or replicate itself across the Internet. Here are some of the most common types of malware;
Macro viruses — These viruses infect applications such as Microsoft Word or Excel. Macro viruses attach to an application’s initialization sequence. When the application is opened, the virus executes instructions before transferring control to the application. The virus replicates itself and attaches to other codes in the computer system.
File infectors — File infector viruses usually attach themselves to an executable code, such as .exe files. The virus is installed when the code is loaded. Another version of a file infector associates itself with a file by creating a virus file with the same name, but a .exe extension. Therefore, when the file is opened, the virus code will execute.
System or boot-record infectors — A boot-record virus attaches to the master boot record on hard disks. When the system is started, it will look at the boot sector and load the virus into memory, where it can propagate to other disks and computers.
Polymorphic viruses — These viruses conceal themselves through varying cycles of encryption and decryption. The encrypted virus and an associated mutation engine are initially decrypted by a decryption program. The virus proceeds to infect an area of code. The mutation engine then develops a new decryption routine and the virus encrypts the mutation engine and a copy of the virus with an algorithm corresponding to the new decryption routine. The encrypted package of mutation engine and virus is attached to new code, and the process repeats. Such viruses are difficult to detect but have a high level of entropy because of the multiple modifications of their source code. Anti-virus software or free tools like Process Hacker can use this feature to detect them.
Stealth viruses — Stealth viruses take over system functions to conceal themselves. They do this by compromising malware detection software so that the software will report an infected area as being uninfected. These viruses conceal any increase in the size of an infected file or changes to the file’s date and time of the last modification.
Trojans — A Trojan or a Trojan horse is a program that hides in a useful program and usually has a malicious function. A major difference between viruses and Trojans is that Trojans do not self-replicate. In addition to launching attacks on a system, a Trojan can establish a back door that can be exploited by attackers. For example, a Trojan can be programmed to open a high-numbered port enabling the hacker to use it to listen and then perform an attack.
Logic bombs — A logic bomb is a type of malicious software that is appended to an application and is triggered by a specific occurrence, such as a logical condition or a specific date and time.
Worms — Worms differ from viruses as in that, they do not attach to a host file but are self-contained programs that propagate across networks and computers. Worms are commonly spread through email attachments. Opening the attachment activates the worm program. A typical worm exploit involves the worm sending a copy of itself to every contact in an infected computer’s email address. In addition to conducting malicious activities, a worm spreading across the internet and overloading email servers can result in denial-of-service attacks against nodes on the network.
Droppers — A dropper is a program used to install viruses on computers. In many instances, the dropper is not infected with malicious code and, therefore might not be detected by virus-scanning software. A dropper can also connect to the internet and download updates to virus software that is resident on a compromised system.
Ransomware — Ransomware is a type of malware that blocks access to the victim’s data and threatens to publish or delete it unless a ransom is paid. While some simple computer ransomware can lock the system in a way that is not difficult for a knowledgeable person to reverse, more advanced malware uses a technique called crypto viral extortion, which encrypts the victim’s files in a way that makes them nearly impossible to recover without the decryption key.
To be continued…
Quote for the day
Positive thinking will let you do everything better than negative thinking will.
- Zig Ziglar