
Day Thirty Seven of CET Crash Course for CET Aspirants
This space gives a glimpse of the Day-Wise information related to CET Crash Course organized for CET Aspirants at 10:00 am to 1:00 pm every day.
Subject: Physics
Topic: Units and dimension +Laws of the Motion
Participant Count: 1,123
Top 10 Most Common Types of Cyber Attacks
A cyber-attack is any type of offensive action that targets computer information systems, infrastructures, computer networks or personal computer devices, using various methods to steal, alter or destroy data or information systems.
 Types of Attacks:
Types of Attacks:
1. Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks
2. Man-in-the-middle (MitM) attack
3. Phishing and spear phishing attacks
4. Drive-by attack
5. Password attack
6. SQL injection attack
7. Cross-site scripting (XSS) attack
8. Eavesdropping attack
9. Birthday attack
10. Malware attack
1. Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks:
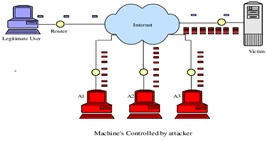
A denial-of-service attack overwhelms a system’s resources so that it cannot respond to service requests. A DDoS attack is also an attack on system’s resources, but it is launched from a large number of other host machines that are infected by malicious software controlled by the attacker.
2. Man-in-the-middle (MitM) attack:
A MitM attack occurs when a hacker inserts itself between the communications of a client and a server.
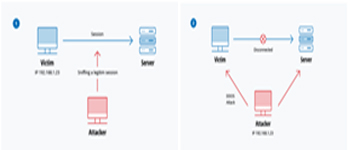 Session hijacking:
Session hijacking:
In this type of MitM attack, an attacker hijacks a session between a trusted client and network server. The attacking computer substitutes its IP address for the trusted client while the server continues the session, believing it is communicating with the client. For instance, the attack might unfold like this:
• A client connects to a server.
• The attacker’s computer gains control of the client.
• The attacker’s computer disconnects the client from the server.
• The attacker’s computer replaces the client’s IP address with its own IP address and
• spoofs the client’s sequence numbers.
• The attacker’s computer continues dialog with the server and the server believes it is still communicating with the client.
To be Continued…
By,
Prof. Madhu R
Dept. of Information Science & Engineering
Quote for the day
No one is perfect - that’s why pencils have erasers.
-Wolfgang Riebe