Placement and Training
Invenger Recruitment

Invenger has job requirement for BE/B.Tech/ME/M.Tech (CS/IS/E&C), MCA, MSc (CS) for the post of CRM Developer (Knowledge on PHP basics), Tech Support Engineer (Knowledge on C, C++ Basics), Devops Engineer (Knowledge on configuration, Application). Candidates hired at Invenger Technologies will be offered a pay package of INR 2.5 LPA – 3 LPA.
About Company:
Invenger Inc is a fast growing IT services company that enhances its customer experience with a committed focus towards providing higher performance and better quality. Key to Invenger's market advantage is its integrated delivery model, which is a combination of a high level of expertise in various businesses, technology, management areas and a customized implementation of best practices to meet every challenge that our clients face.
BPCL Hiring

Bharat Petroleum Corporation Ltd., Kochi Refinery, Ambalamugal, Kochi invites Online application from eligible Graduate & Diploma holders in Engineering (passed during 2019, 2O2O & 2021) for undergoing one year Apprenticeship training under the Apprenticeship (Amendment Act 1973). Package which offered is INR 25,000 P.M
About Company:
Bharat Petroleum Corporation Limited (BPCL) is an Indian government-owned oil and gas corporation. It is under the ownership of Ministry of Petroleum and Natural Gas, Government of India, headquartered in Mumbai, Maharashtra. It operates two large refineries in Kochi and Mumbai. India's second-largest downstream oil company, it was ranked 309th on the 2020 Fortune list of the world's biggest corporations, and 792nd on Forbes's 2021 "Global 2000" list.

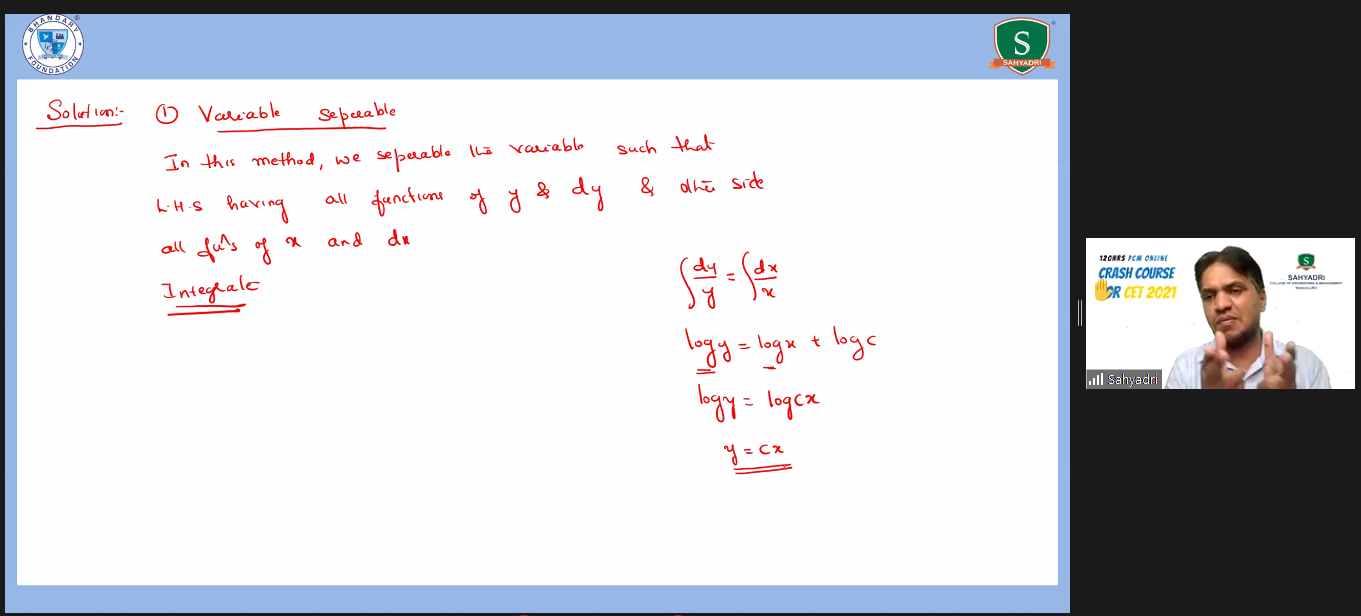
Day Thirty Eight of CET Crash Course for CET Aspirants
This space gives a glimpse of the Day-Wise information related to CET Crash Course organized for CET Aspirants at 10:00 am to 1:00 pm every day.
Subject: Mathematics
Topic: Application of Integration and Differential equations
Participant Count: 1,358
Top 10- Most Common Types of Cyber Attacks
Continued...
3. Phishing and spear phishing attacks:
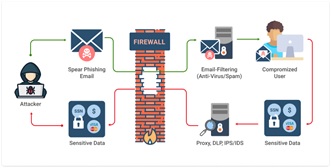
Phishing attack is the practice of sending emails that appear to be from trusted sources with the intent of acquiring personal information or influencing users to do something for the senders gain. It’s a combination of social engineering and technical trickery. It could involve an attachment to an email that automatically loads malware onto your computer, orcould also be a link to an illegitimate website that can trick you into downloading malware or handing over your personal information unknowingly.
So How do we reduce the risk of being phished, one can use the below mentioned techniques;
• Critical thinking — Do not accept every email to be the real deal just because you’re busy, stressed-out or you have 150 unread messages in your inbox. Stop for a minute, think and analyse the email.
• Hovering over the links — Move your mouse over the link, but do not click it! Just let your mouse cursor hover over the link and see where it will actually leadyou. Apply critical thinking to decipher the URL.
• Analysing email headers — Email headers define how an email got to your address. The “Reply-to” and “Return-Path” parameters should lead to the same domain as it’s stated in the email.
• Sandboxing — You can test email content in a sandbox environment, logging activity from opening the attachment or clicking the links inside the email.
• Drive-by attack:
Drive-by download attacks are a common method of spreading malware. Hackers look for insecure websites and plant a malicious script into HTTP or PHP code on one of the pages. This script might install malware directly onto the computer of someone who visits the site, or it might re-direct the victim to a site controlled by the hackers. Drive-by downloads can happen when visiting a website or viewing an email message or a pop-up window. Unlike many other types of cyber security attacks, a drive-by doesn’t rely on a user to do anything to actively enable the attack — you don’t have to click a download button or even open a malicious email attachment to become infected. A drive-by download can take advantage of an app, operating system or web browser that contains security flaws due to unsuccessful updates or lack of updates.
To protect yourself from drive-by attacks, you need to keep your browsers and operating systems up to date and avoid websites that might contain malicious code. Stick to the sites you normally use — Having said that, keep in mind that even these sites aren’t safe and can be hacked. Don’t keep too many unnecessary programs and apps on your device. The more plug-ins you have, more the presence of vulnerabilities on your system that can be exploited by drive-by attacks.
To be continued…
Quote for the day
Positive thinking will let you do everything better than negative thinking will.
- Zig Ziglar